The Future of MFA Authentication and How Archer & Round Can Help
Introduction
The future of multi-factor authentication (MFA) is evolving rapidly. As cyber threats become more sophisticated, traditional authentication methods like passwords and basic two-factor authentication (2FA) are proving inadequate. This article explores the latest advancements in MFA, including FIDO2, U2F, WebAuthn, and passkeys, and highlights how Archer & Round can help businesses implement the most secure authentication solutions.
The Problem with Traditional Authentication
For years, authentication has relied on a mix of passwords, SMS-based 2FA, and other knowledge-based factors. However, these methods are vulnerable to phishing, man-in-the-middle attacks, and credential theft. Even time-based one-time passwords (TOTP) from apps like Google Authenticator and Authy have weaknesses, as attackers can trick users into providing these codes through social engineering.
The Shift to Phishing-Resistant Authentication
Modern authentication standards, such as WebAuthn and FIDO2, offer a phishing-resistant approach. These standards use cryptographic key pairs, ensuring that only the legitimate website can authenticate a user. Unlike traditional MFA, where users manually enter a code, WebAuthn automates the authentication process securely without exposing sensitive data to attackers.
How WebAuthn Authentication Works
WebAuthn authentication relies on a secure flow that eliminates the need for passwords. Here’s a simplified overview of the process:
- User Registration: The user registers with a website using a device that supports WebAuthn, such as a security key or biometric-enabled device.
- Key Pair Generation: A cryptographic key pair (public and private) is created. The private key remains on the user’s device, while the public key is shared with the website.
- Authentication Request: When the user attempts to log in, the website sends a challenge request.
- User Verification: The user verifies their identity using biometrics (fingerprint or facial recognition) or a hardware security key.
- Authentication Completion: The device signs the challenge using the private key and sends it back to the website, confirming the user’s identity.
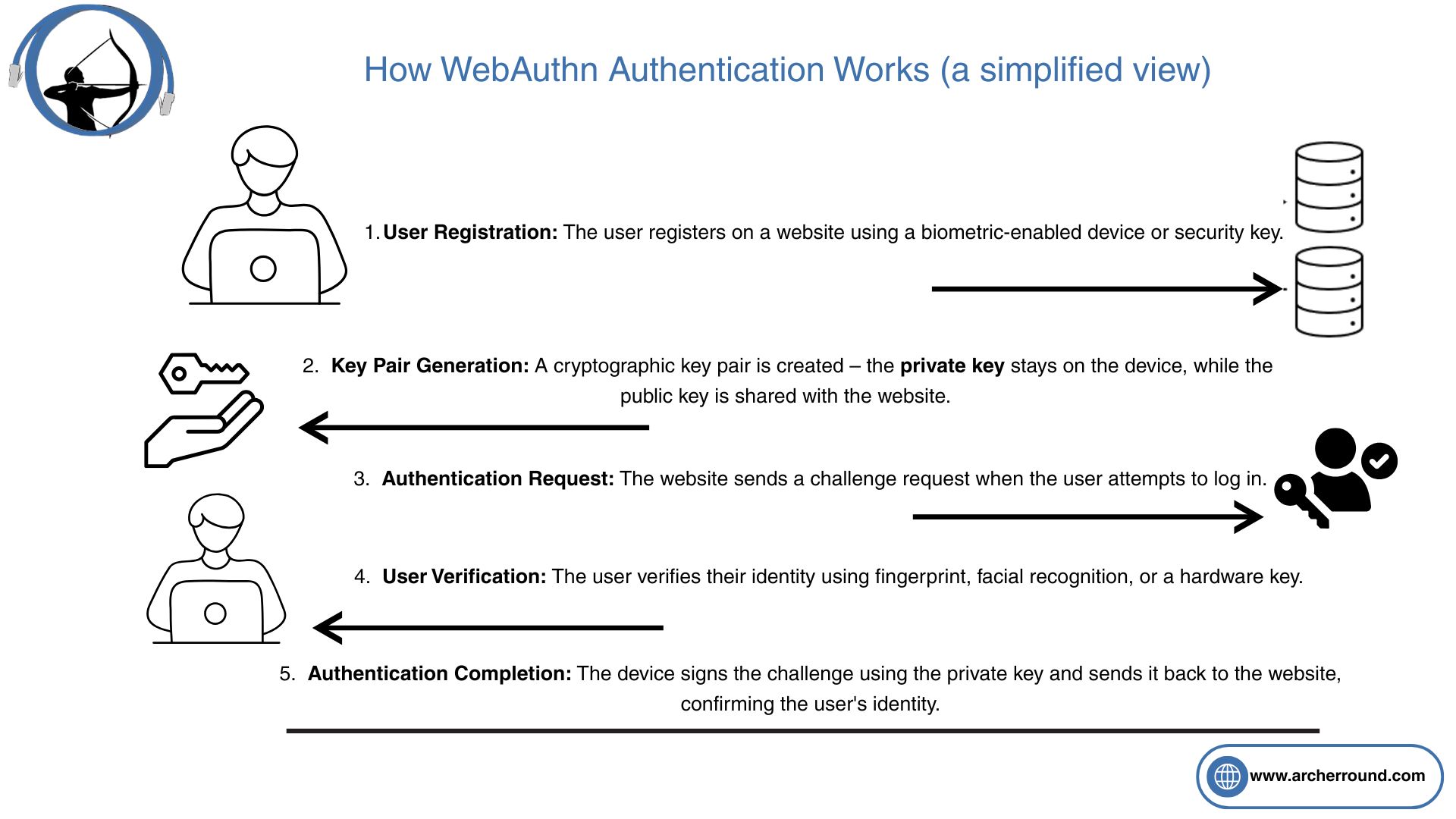
By eliminating passwords and one-time codes, WebAuthn significantly reduces the risk of phishing attacks and credential theft.
How Archer & Round Can Help
Archer & Round specializes in implementing cutting-edge authentication solutions that enhance security while maintaining user convenience. Their expertise includes:
- Deploying advanced passwordless authentication methods for enhanced security
- Implementing phishing-resistant multi-factor authentication (MFA) solutions
- Integrating secure authentication mechanisms across devices and platforms
- Enhancing enterprise security through modern identity verification strategies
- Providing tailored cybersecurity consulting to prevent credential theft
- Educating businesses on the benefits of frictionless authentication for improved user experience
The Future of Authentication
The adoption of passwordless authentication is growing as organizations recognize its benefits. By leveraging WebAuthn, businesses can create a seamless, phishing-resistant login experience that strengthens security and improves user experience. This transition is crucial in the fight against cyber threats.
Learn More
For a deeper dive into modern authentication methods, check out these resources:




